Flood Shield は、分散サービス拒否攻撃 (SYN フラッド、ACK フラッド、UDP フラッド、HTTP フラッドなど) に対して配信元の安定性を確保するために、迅速、シンプル、かつ効果的な DDoS 保護を提供する包括的なクラウドベースの DDoS 保護サービスです。 .) リアルタイムで。同時に、正当なユーザーにアクセラレーション サービスを提供して、全体的なカスタマー エクスペリエンスを最適化します。このソリューションは、オンライン サービスとインフラストラクチャの安定性と信頼性を確保するためのシールドとして機能します。
Flood Shield は、米国、ヨーロッパ、アジア、中国本土にあるデータセンターを備えた CDNetworks の巨大なグローバル インフラストラクチャに導入されています。 20 を超えるグローバル DDoS スクラビング センターと 15 Tbps の総容量を備え、最も高度で大規模な大量攻撃からも Web サイト、Web アプリ、ネットワーク インフラストラクチャを保護できるように設計されています。
20 以上のグローバル DDoS スクラビング センター
15 Tbps 以上の緩和能力
SYNフラッド、ACKフラッド、ICMPフラッド、UDPフラッド、HTTPフラッド、SlowLoris攻撃など、レイヤ34およびレイヤ7DDoS防御機能。
アクセスポリシーとレート制限を事前にカスタマイズして、攻撃やリソースの乱用を回避します。
事前に設定された3つのDDoS攻撃保護モードを使用でき、さまざまなタイプの攻撃に対応する際に切り替えが容易です。
L3/4およびL7DDoS攻撃アラートを含むWebサイトの異常を迅速に通知する総合的なモニタリングおよびアラートサービス。
HTTPHTTPSおよびTCPUDPプロトコルは、さまざまなビジネスタイプを満たすためにサポートされています。
お客様のリスクプロファイルに合わせて設計された柔軟な価格設定モデルを提供し、お客様のビジネスニーズに最も効果的な方法でお支払いいただけます。 予算によって選択できる無制限の緩和策と弾力的な緩和策がありまる。
オリジンサーバーの実際のIPアドレスを完全に隠すことで、サーバーのセキュリティを強化します。 その結果、攻撃者はオリジンサーバーを直接攻撃するためのオリジンIPを識別できません。 また、ホワイトリストに追加して不要な要求を遮断し、セキュリティレベルをさらに高めるグローバルPoPのIPも提供します。
CDNetworks のコンテンツ配信ネットワーク (CDN) は、何千もの大規模なグローバル企業にサービスを提供し、大量のアクセス データや攻撃/防御サンプルを含む TB 規模のログ データを毎日処理しています。プラットフォームのビッグ データと機械学習機能は、ネットワーク攻撃の傾向をリアルタイムで検出し、防御を事前に自動的に有効化するのに役立ちます。また、攻撃をインテリジェントに分析して識別し、IP アドレス、HTTP ヘッダー、Cookie、JavaScript スニペットなどを含む正当なトラフィックの通常の動作をモデル化します。
CDNetworksは、DDoS対策、WAF(Webアプリケーションファイアウォール)、API security、ゲートウェイ、Bot管理、特定の攻撃防御モジュールなどを網羅し、サービスやアプリケーションを保護する包括的なマルチ・レイヤ・セキュリティ・ソリューションを提供します。一つのポータルで複数の製品を利用することで、保守コストを大幅に削減するとともに、お客様のチームでの運用を簡素化することができます。
20 を超えるグローバル DDoS スクラビング センターと 15 Tbps の総容量を備えた Flood Shield は、最も高度で大規模な大量攻撃からも Web サイトとネットワーク インフラストラクチャを保護するように設計されています。
グローバルサーバ
グローバルCDN PoP
国と地域
スクラビングキャパシティ
スクラビングセンタ
『Flood Shield』のDDoS防御テクノロジーは、CDNetworksの分散型PoP(Point of Presence)上に展開されます。これは事実上無制限の容量を持つ、クラウドベースの常時接続ミティゲーション サービスです。ネットワークに高度なデプロイメントや変更を加える必要はなく、スムースなスケーリング自動化を提供します。
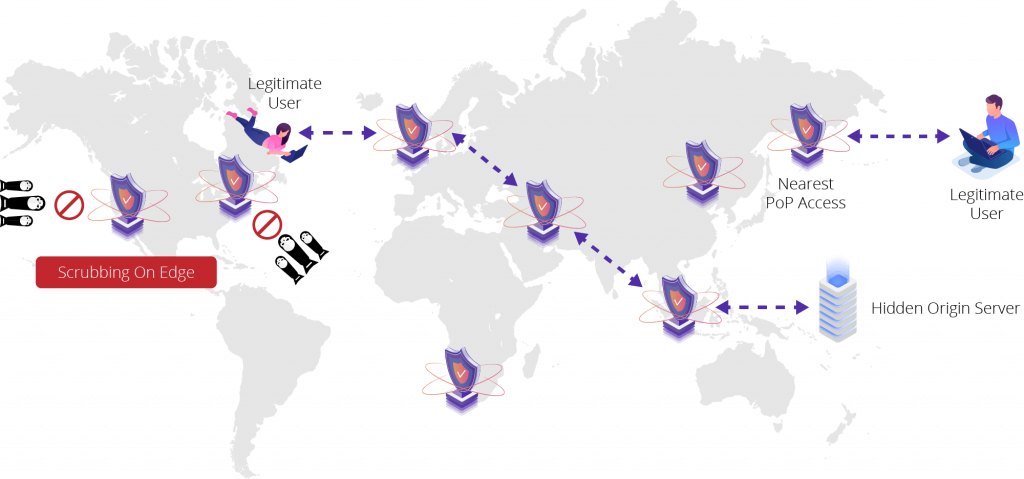
『Flood Shield』は、シンプルなDNSの変更によって提供され、通常、ウェブサイト/HTTP&HTTPSトラフィック、および複数のドメイン/サーバ/プロトコルを含むネットワークインフラ全体を保護します。顧客トラフィックがCDNetworksのPoPを経由することでDDoS攻撃は顧客サーバやネットワークではなく、CDNetworksのインフラストラクチャを攻撃します。CDNetworksのPoPは、アプリケーション層(L7)と既知のすべてのタイプのネットワーク層(L3/L4)の両方の攻撃を検出し、防御することができます。
当社のウェブサイトでよりパーソナライズされた効率的なブラウジング体験を提供するために、当社はクッキーやその他の類似の技術を使用して、お客様、お客様の好み、お客様が使用するデバイスに関する特定の情報を収集することがあります。 CDNetworks プライバシーポリシー.